At Code Craver, we combine artificial intelligence and robust security to safeguard and optimize your digital assets.
We implement AI-powered threat detection and automated defense mechanisms to keep your systems secure.
From firewalls to encryption, we deploy cutting-edge security measures to protect sensitive data.
We develop intelligent AI models that analyze patterns, detect anomalies, and optimize business performance.
Stay ahead of cyber threats with proactive monitoring and instant response solutions.
We embed AI into security frameworks to create smarter, more adaptive defense systems.

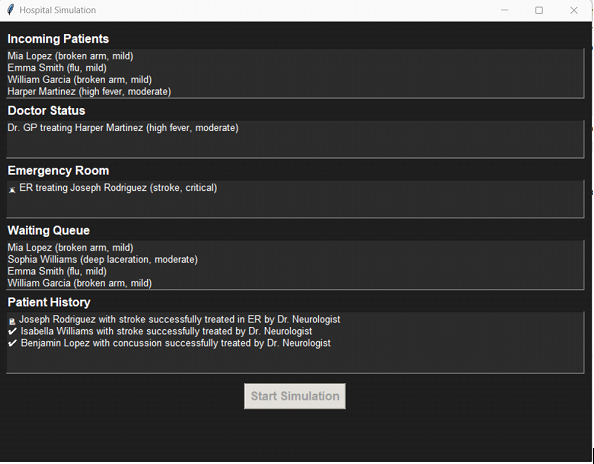
Developed a hospital management simulation system with a graphical user interface (GUI) to track patient intake, doctor status, emergency room activity, and patient history

Description: Conducted practical cryptographic operations using OpenSSL, including file encryption, digital signatures, and secure communication.
Technologies Used: OpenSSL, Command Line, Cryptography

Enhanced Understanding of Application Security: Through this project, We gained a deeper understanding of common security vulnerabilities in web applications and the techniques used to mitigate them

Following host discovery techniques were required to be incorporated through our developed tool:
1. ARP Ping Scan
2. ICMP Ping Scan
o ICMP Echo Ping
o ICMP Echo Ping Sweep
o ICMP Timestamp Ping
o ICP Address Mask Ping

Following port discovery techniques must be incorporated through your developed tool:
1. TCP Scan
SYN Scan (Full Open Scan)
Stealth Scan (Half Open Scan)
o Inverse TCP Flag Scan
FIN Scan
Null Scan
XMAS Scan
Maimon Scan
o ACK Flag Scan
TTL Based Scan
Window Scan
Threat Analysis – We conduct in-depth assessments to identify security vulnerabilities and AI opportunities.
AI-Powered Security Solutions – We design intelligent cybersecurity frameworks with predictive analytics and automated defense mechanisms.
Custom AI Model Planning – We strategize AI implementations, from automation to fraud detection and real-time data insights.
Cybersecurity Integration – We implement advanced encryption, intrusion detection, and automated threat mitigation.
Machine Learning & AI Deployment – We develop AI solutions that enhance cybersecurity protocols and business intelligence.
Real-Time Monitoring & Automation – We enable AI-driven analytics and proactive threat response to keep systems secure and efficient.
Live Monitoring & Incident Response – We provide 24/7 security monitoring to prevent cyber threats before they escalate.
Regular Security Updates & AI Enhancements – We refine AI models and security frameworks to keep up with evolving threats.
Ongoing Optimization – We analyze data trends and fine-tune AI security measures to maintain peak efficiency.

Connect Us